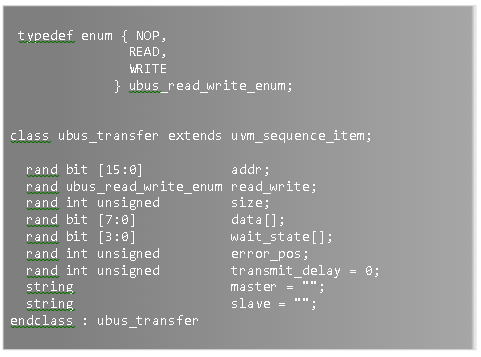
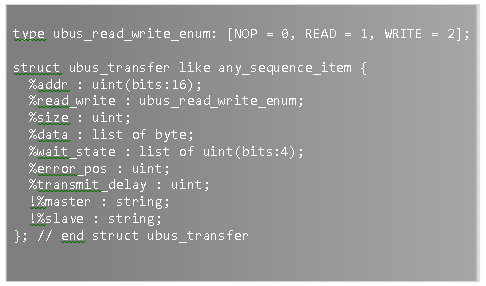
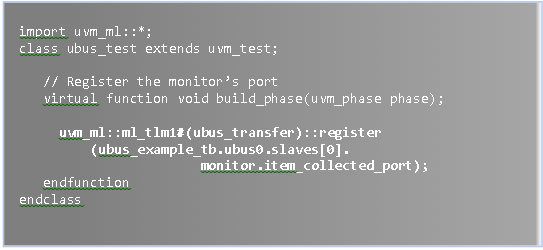
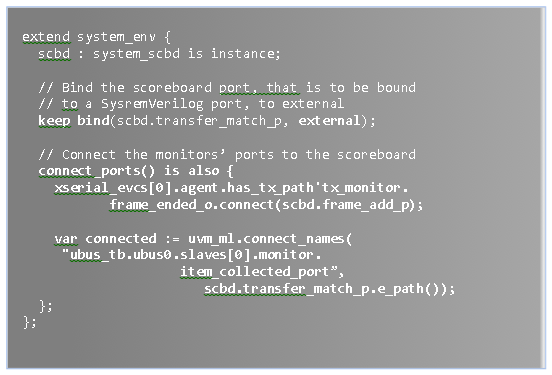
Every modern device, even the ones with modest complexity, could never be developed by a single person at the quality, cost, and performance levels we enjoy today. This has been true for over 100 years – since the Industrial revolution.
Modern product development is highly dependent on knowledge, research, and engineering skills developed in the past. Furthermore, not a single company is able to go it alone anymore. The complexities and the layers in modern devices are truly mind-boggling and involve disciplines like physics, chemistry, engineering, design, and even management.
For a modern company to be successful, the key question is what to develop in-house, what to buy, or when to look for a partner.
These decisions are highly complex and are a fundamental part of making a company successful. Further on, these decisions have to be reexamined all the time as markets are continuously evolving.
Companies that successfully master these decisions can survive in the long run. Others will vanish. Companies have to determine where their sweet spot is for adding value, and cannot rest forever on that spot because the future will catch up with them very quickly.
A prime example of a company with many interdependencies is Dell. At the beginning of the PC revolution, we had Intel and others developing and selling the core hardware components like CPUs and supporting chips. We had Microsoft creating the dominant operating system: MS-DOS and later Windows, and Office, the most popular and successful application software package. Neither Intel nor Microsoft sold PCs. They focused on their respective core competencies, and still do this today.
Dell saw an opening in building PCs from the core technologies delivered by Intel, Microsoft, and others, and thus became a master of supply chain management and distribution. At their peak Dell had an astounding market share and was very clever and profitable for years.
But then the PC market changed, and profit margins shrank significantly. Profitable growth in the PC market became harder to attain. Eventually, Dell struggled more and more just to get compensated for the value they delivered and the core competency they held. Today, Dell is a shadow of its former self because they were unable to reinvent themselves in ways the market demanded.
Reinvention is not optional. It is a requirement to stay competitive and profitable.
A counter example to the Dell story is IBM. They are proactively trying to adapt to ever-changing business conditions. Unlike Dell, IBM foresaw the declining trend in the PC industry and divested of it a long time ago by selling their PC division to Lenovo. IBM continued to do this. Right now they are in the process of divesting significant sections of their microelectronic business by selling it to GLOBALFOUNDRIES, formerly the semiconductor division of AMD.
Being proactive about managing change is just a necessary business condition. However, it is not sufficient to guarantee success. How to enable change successfully and, thus, how to win, is where the true magic in business can be found.
After the return in 1997 of Steve Jobs to Apple, we saw an unprecedented success story in change management. Even before Apple’s multiple transformations, we have seen other reformers like Lee Iacocca at Chrysler changing the mode of operation of a complete company. But at Chrysler, and many others, the change that occurred was not sustained and did not become a cornerstone of the company culture.
Apple is the archetype in adapting to new markets. They are extremely proactive in pushing for change, and would rather cannibalize their own product lines to prevent the competition getting ahead of them. This can been seen in the evolution of the various iPod lines, which was the first significant foray out of the core business of personal computing. It was followed up by the iPhone, which is still extremely successful and profitable beyond any expectations.
In all of these transitions and changes, Apple was very deliberate about what it did and which products it brought to market. The original Macintosh, introduced in 1984, was running on a Motorola processor. At the time that might have been a good choice. However, over time Motorola could not compete with Intel, and Apple was nervously sweating it out.
In response to Intel’s dominance, Apple created a partnership with IBM and Motorola, called AIM, whose charter was to derive technology from IBM’s workstation processors in order to create a new generation of RISC CPUs to power the Macintosh line, which was called the PowerPC. One amazing aspect of this transition was that Apple kept the code base and existing software fully functional, without losing the support of third-party software companies.
For a few years this actually worked. But after some time Apple again found itself in the same dilemma - AIM could not compete with Intel in the CPU business. Consequently, Apple did the unthinkable and switched the processor architecture for the second time, now from PowerPC to the x86 platform. And, the craziest part about this is that they survived both complex transitions, including the sustained support from key software application vendors such as Microsoft!
In more recent history, Apple has made other bold decisions and come out on top. The original iPhone was powered by an SoC (the most important component of the hardware) developed by Samsung. However, Apple quickly realized that the SoC is a key part of the product puzzle that it needs to keep control of in order to stay competitive. They did not want to be dependent on Motorola, IBM, Intel, Samsung, or anyone else for a key component of their flagship product again. This made perfect economic sense, since the high volume of iPhone sales is in a totally different cost and profit ballpark than Mac sales.
Thus, Apple went ahead and acquired a few small CPU houses that develop chips using ARM CPU cores. They integrated those companies very quickly and are now themselves transformed into a formidable SoC development house. In fact, Apple pioneered 64-bit SoCs in the mobile market, and they managed to make their SoC in the iPhone 6 the fastest mobile SoC in the market.
When I hear business analysts or car industry experts say that Apple will not be able to develop an automobile, it shows me that they really do not understand this company and its potential. The core of their misunderstanding is that they believe that cars are made primarily from metal and, therefore, the core competency in car development ought to be mechanical engineering and heavy industrial manufacturing. But, remember, what you don’t develop in-house you can buy, or you can team up with a partner.
This assumption might have been true years ago. But cars today are no longer predominantly mechanical devices. They are dominated by electronics. Most car manufacturers are still very slow to understand this and to change their approach to business. And, if they do not adapt quickly, their competitiveness will change in fundamental ways because if it is not Apple, it will be another company that will bring their electronics, and system and software integration expertise, to play to give established car manufacturers a real run for their money. This is the main point of the car product puzzle – There will be electrons!
After this transition, some car companies will be shadows of themselves, and might not survive the transformation. Others will wake up to this new competition and transform themselves in order to stay in business. Market forces will bring about this change on a significant scale.
Apple made the decision to develop their own mobile SoCs. They also write their own operating system and application software. They only buy parts that are not key to differentiation. If Apple decides to step into the automotive space they will bring their core competencies into play. They transformed OS X from a PC operating system (OS) to a mobile OS, and this was not just an adaption. They will create, or derive, an OS for the car and they will develop and integrate the key car SoCs and software technology themselves.
No matter what Apple decides to do and how to do it, the car industry had better watch out. Electronics and software are the key for future innovation in most spaces, and in particular in the car industry.
Axel Scherer
Twitter: @axelscherer
![]()
![]()